Akamai recently released their 2019 State of the Internet / Security Report and in it detailed how criminals are leveraging a range of domain extensions to trick their victims. If you don’t know what phishing is, think of it as essentially trying to trick someone into giving you their username or password, often by pretending to be someone you’re not.
Back in the early days of computer hacking, phishing was actually done over the phone. A hacker (at that time often called Phone Phreaker) would call someone on the phone pretending to be say, an admin from AOL. They would then tell the user that there was a problem with their account and they needed their login and password to get everything fixed. As technology progressed, so did phishing schemes and today many of them are hosted on confusingly similar domains to make users think they’re actually logging in on a real company website when in fact they’re just giving away their user credentials to a hacker.
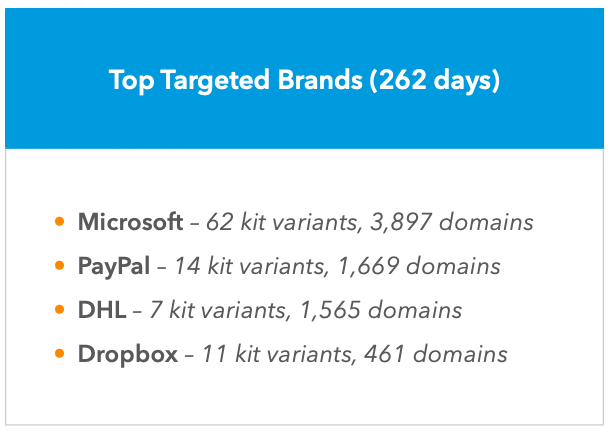
While phishing attacks target a lot of different company’s users, Microsoft took the cake with 20% of the domains. Here’s a look at the top four from the report:
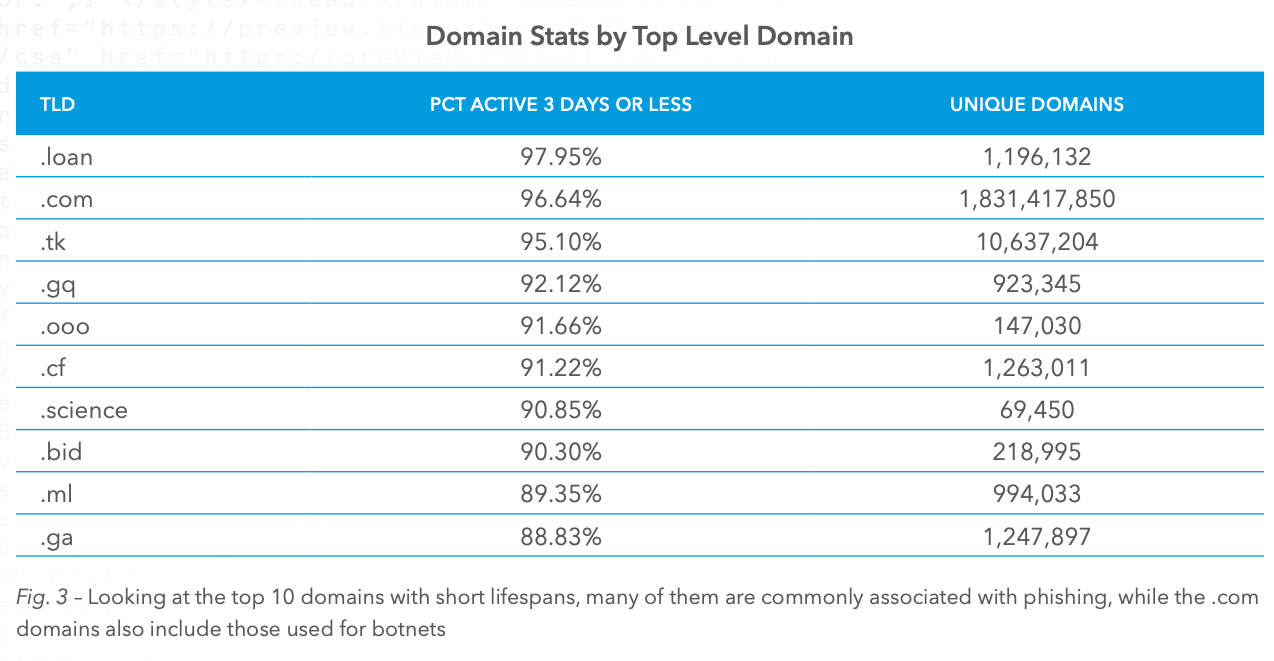
When it comes to the domain names that are used for phishing attacks it should come as no surprise that .COM is the most-used by a pretty wide margin. If you think about it from the hackers perspective, they want the user to be confused and think they are on a real company website and .COM is what people do know and trust the most.
At the same time, hackers are cheap and often will gravitate towards domain names that offer specials, i.e. promotions where they can buy lots of domains for a dollar or two. Here’s the full list of the top domain extensions used for phishing:
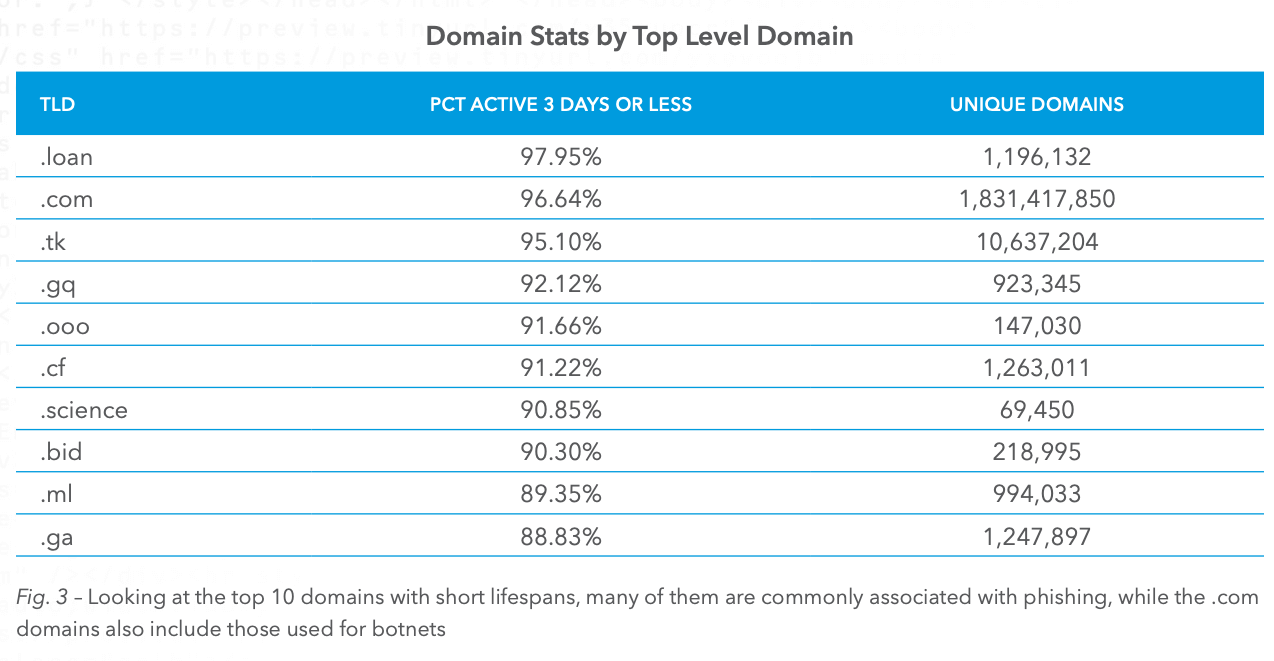
I was pretty surprised to see .SCIENCE on this list, but at the same time, I’m guessing that criminals feel this might be a particularly trustworthy sounding domain extension, or at least that’s my thought. The domain extension that I was the least surprised to see was .TK, it has been one of the most scammy domain extensions out there for a long time so it makes sense to find it in the top three.
The moral of the story here is relatively simple. If you click on a link and land on a site that doesn’t quite look right, it probably isn’t. Even if the site is on a .COM domain, look at the spelling of the domain name, check the SSL cert, be careful anytime you enter your password. This is also why password managers like Dashlane and 1Password are so handy, if you’re not a legitimate site it won’t populate your password.
Were you surprised to see any of the domain extension on the list? I want to hear from you, comment and let your voice be heard!